What else would they say?
Internet giants deny granting government 'direct access' to servers
AP survey: Economists see no stock market bubble
Here's where the very last of the Left leave the party and a real leader exposes Obama's Bush III governing:
I hope Glenn Greenwald has a nice place already picked out either in a country without extradition treaties with the US or is so lawyered up (and what lawyers would they be?) that he's invisible (to the metadata captors), notwithstanding his appearance on last Sunday's lamestream media delight (for the delight of the still believing).
NSA Taps In To User Data of Facebook, Google and Others, Secret Files Reveal
• Top secret PRISM program claims direct access to servers of firms including Google, Facebook and Apple
• Companies deny any knowledge of program in operation since 2007
By Glenn Greenwald and Ewen MacAskill
June 07, 2013 "Information Clearing House - "The Guardian" - The National Security Agency has obtained direct access to the systems of Google, Facebook, Apple and other US internet giants, according to a top secret document obtained by the Guardian.
The NSA access is part of a previously undisclosed program called PRISM, which allows officials to collect material including search history, the content of emails, file transfers and live chats, the document says.
The Guardian has verified the authenticity of the document, a 41-slide PowerPoint presentation – classified as top secret with no distribution to foreign allies – which was apparently used to train intelligence operatives on the capabilities of the program. The document claims "collection directly from the servers" of major US service providers.
Although the presentation claims the program is run with the assistance of the companies, all those who responded to a Guardian request for comment on Thursday denied knowledge of any such program.
In a statement, Google said: "Google cares deeply about the security of our users' data. We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government 'back door' into our systems, but Google does not have a back door for the government to access private user data."
Several senior tech executives insisted that they had no knowledge of PRISM or of any similar scheme. They said they would never have been involved in such a program. "If they are doing this, they are doing it without our knowledge," one said.
An Apple spokesman said it had "never heard" of PRISM.
The NSA access was enabled by changes to US surveillance law introduced under President Bush and renewed under Obama in December 2012.
 The program facilitates extensive, in-depth surveillance on live communications and stored information. The law allows for the targeting of any customers of participating firms who live outside the US, or those Americans whose communications include people outside the US.
The program facilitates extensive, in-depth surveillance on live communications and stored information. The law allows for the targeting of any customers of participating firms who live outside the US, or those Americans whose communications include people outside the US.
It also opens the possibility of communications made entirely within the US being collected without warrants.
Disclosure of the PRISM program follows a leak to the Guardian on Wednesday of a top-secret court order compelling telecoms provider Verizon to turn over the telephone records of millions of US customers.
The participation of the internet companies in PRISM will add to the debate, ignited by the Verizon revelation, about the scale of surveillance by the intelligence services. Unlike the collection of those call records, this surveillance can include the content of communications and not just the metadata.
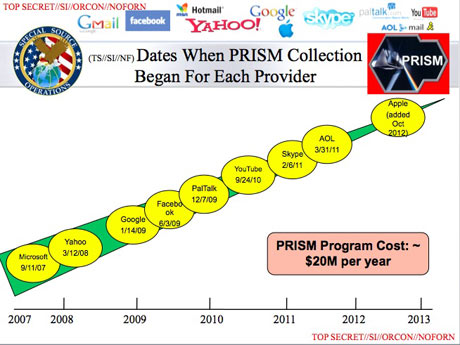
Some of the world's largest internet brands are claimed to be part of the information-sharing program since its introduction in 2007. Microsoft – which is currently running an advertising campaign with the slogan "Your privacy is our priority" – was the first, with collection beginning in December 2007.
It was followed by Yahoo in 2008; Google, Facebook and PalTalk in 2009; YouTube in 2010; Skype and AOL in 2011; and finally Apple, which joined the program in 2012. The program is continuing to expand, with other providers due to come online.
Collectively, the companies cover the vast majority of online email, search, video and communications networks.
The extent and nature of the data collected from each company varies.
Companies are legally obliged to comply with requests for users' communications under US law, but the PRISM program allows the intelligence services direct access to the companies' servers. The NSA document notes the operations have "assistance of communications providers in the US".
The revelation also supports concerns raised by several US senators during the renewal of the Fisa Amendments Act in December 2012, who warned about the scale of surveillance the law might enable, and shortcomings in the safeguards it introduces.
When the FAA was first enacted, defenders of the statute argued that a significant check on abuse would be the NSA's inability to obtain electronic communications without the consent of the telecom and internet companies that control the data. But the PRISM program renders that consent unnecessary, as it allows the agency to directly and unilaterally seize the communications off the companies' servers.
A chart prepared by the NSA, contained within the top-secret document obtained by the Guardian, underscores the breadth of the data it is able to obtain: email, video and voice chat, videos, photos, voice-over-IP (Skype, for example) chats, file transfers, social networking details, and more.
The document is recent, dating to April 2013. Such a leak is extremely rare in the history of the NSA, which prides itself on maintaining a high level of secrecy.
The PRISM program allows the NSA, the world's largest surveillance organisation, to obtain targeted communications without having to request them from the service providers and without having to obtain individual court orders.With this program, the NSA is able to reach directly into the servers of the participating companies and obtain both stored communications as well as perform real-time collection on targeted users.
The presentation claims PRISM was introduced to overcome what the NSA regarded as shortcomings of Fisa warrants in tracking suspected foreign terrorists. It noted that the US has a "home-field advantage" due to housing much of the internet's architecture. But the presentation claimed "Fisa constraints restricted our home-field advantage" because Fisa required individual warrants and confirmations that both the sender and receiver of a communication were outside the US.
"Fisa was broken because it provided privacy protections to people who were not entitled to them," the presentation claimed. "It took a Fisa court order to collect on foreigners overseas who were communicating with other foreigners overseas simply because the government was collecting off a wire in the United States. There were too many email accounts to be practical to seek Fisas for all."
The new measures introduced in the FAA redefines "electronic surveillance" to exclude anyone "reasonably believed" to be outside the USA – a technical change which reduces the bar to initiating surveillance.
The act also gives the director of national intelligence and the attorney general power to permit obtaining intelligence information, and indemnifies internet companies against any actions arising as a result of co-operating with authorities' requests.
In short, where previously the NSA needed individual authorisations, and confirmation that all parties were outside the USA, they now need only reasonable suspicion that one of the parties was outside the country at the time of the records were collected by the NSA.
The document also shows the FBI acts as an intermediary between other agencies and the tech companies, and stresses its reliance on the participation of US internet firms, claiming "access is 100% dependent on ISP provisioning".In the document, the NSA hails the PRISM program as "one of the most valuable, unique and productive accesses for NSA".
It boasts of what it calls "strong growth" in its use of the PRISM program to obtain communications. The document highlights the number of obtained communications increased in 2012 by 248% for Skype – leading the notes to remark there was "exponential growth in Skype reporting; looks like the word is getting out about our capability against Skype". There was also a 131% increase in requests for Facebook data, and 63% for Google.
The NSA document indicates that it is planning to add Dropbox as a PRISM provider. The agency also seeks, in its words, to "expand collection services from existing providers".
The revelations echo fears raised on the Senate floor last year during the expedited debate on the renewal of the FAA powers which underpin the PRISM program, which occurred just days before the act expired.
Senator Christopher Coons of Delaware specifically warned that the secrecy surrounding the various surveillance programs meant there was no way to know if safeguards within the act were working.
"The problem is: we here in the Senate and the citizens we represent don't know how well any of these safeguards actually work," he said.
"The law doesn't forbid purely domestic information from being collected. We know that at least one Fisa court has ruled that the surveillance program violated the law. Why? Those who know can't say and average Americans can't know."
Other senators also raised concerns. Senator Ron Wyden of Oregon attempted, without success, to find out any information on how many phone calls or emails had been intercepted under the program.
When the law was enacted, defenders of the FAA argued that a significant check on abuse would be the NSA's inability to obtain electronic communications without the consent of the telecom and internet companies that control the data. But the PRISM program renders that consent unnecessary, as it allows the agency to directly and unilaterally seize the communications off the companies' servers.
When the NSA reviews a communication it believes merits further investigation, it issues what it calls a "report". According to the NSA, "over 2,000 PRISM-based reports" are now issued every month. There were 24,005 in 2012, a 27% increase on the previous year.
In total, more than 77,000 intelligence reports have cited the PRISM program.Jameel Jaffer, director of the ACLU's Center for Democracy, that it was astonishing the NSA would even ask technology companies to grant direct access to user data.
"It's shocking enough just that the NSA is asking companies to do this," he said. "The NSA is part of the military. The military has been granted unprecedented access to civilian communications.
"This is unprecedented militarisation of domestic communications infrastructure. That's profoundly troubling to anyone who is concerned about that separation."
A senior administration official said in a statement: "The Guardian and Washington Post articles refer to collection of communications pursuant to Section 702 of the Foreign Intelligence Surveillance Act. This law does not allow the targeting of any US citizen or of any person located within the United States.
"The program is subject to oversight by the Foreign Intelligence Surveillance Court, the Executive Branch, and Congress. It involves extensive procedures, specifically approved by the court, to ensure that only non-US persons outside the US are targeted, and that minimize the acquisition, retention and dissemination of incidentally acquired information about US persons.
"This program was recently reauthorized by Congress after extensive hearings and debate.
"Information collected under this program is among the most important and valuable intelligence information we collect, and is used to protect our nation from a wide variety of threats.
"The Government may only use Section 702 to acquire foreign intelligence information, which is specifically, and narrowly, defined in the Foreign Intelligence Surveillance Act. This requirement applies across the board, regardless of the nationality of the target."
Additional reporting by James Ball and Dominic Rushe
'4 Intelligence Officials' Allegedly Joke Of 'Disappearing' NSA Leaker, Reporter
The Huffington Post
By Alana Horowitz
Posted: 06/08/2013 | Updated: 06/09/2013
Leading foreign policy analyst Steve Clemons said he witnessed a rather disturbing conversation while waiting for a flight at the Dulles airport on Saturday.
According to Clemons, four men sitting near him were discussing an intelligence conference they had just attended, and turned to the topic of the NSA leaks. One said that both the reporter and leaker should be "disappeared," a term used to describe secret murders and abductions carried out by authoritarian governments. Clemons said on Twitter the suggestion seemed to be "bravado" and a "disturbing joke." He said that the officials were talking loudly, "almost bragging."
HuffPost asked Clemons via Twitter how he could be sure they were in the intelligence community and he noted that "one wore a white knit national counterterrorism center shirt." But more importantly, he said, the conversation led him to conclude that they were certainly in the community, especially given the conference they talked about attending. They discussed former Ambassador John Negroponte as having been in attendance. (If you know what conference that was, email openreporting@huffingtonpost.com.)
Clemons, who is editor at large at The Atlantic, said he did not know who the officials were or what agency they were with. He recorded part of the conversation and took some photos, which he plans to post online.
The incident comes just days after news broke that the NSA had been obtaining millions of phone records daily. The story was first reported by Glenn Greenwald at the Guardian.
Later this week, it was also reported that the NSA program, PRISM, also tapped into data from several major tech companies, including Google, Apple and AOL (which owns The Huffington Post.)
UPDATE: Clemons has learned that the men were in town attending an event hosted by the Intelligence and National Security Alliance, which lists dress code for the dinner as "black tie or mess dress."
_ _ _ _ _ _ _
What an Overbroad Section 215 Order Looks Like
Glenn Greenwald has a tremendous scoop, for the first time I know of publishing a Section 215 warrant — in this case one asking for all US-based traffic metadata from Verizon Business Services from April until July.
Now, I think that this actually affects just a subset of all Verizon traffic: the business-focused traffic rather than Verizon Wireless or similar consumer products most people subscribe to (and if that’s so, the shitstorm that is about to break out will be all the more interesting given that rich businessmen will be concerned about their privacy for once).
Also, this does not ask for call content. It asks only for metadata, independent of any identifying data.
In other words, they’re using this not to wiretap the conversations of Occupy Wall Street activists but to do pattern analysis on the telecom traffic of (I think) larger businesses.
The request does, however, ask for location data (and Verizon does offer bundles that would include both cell and cloud computing). So maybe the FBI is analyzing where all Verizon’s business customers are meeting for lunch.
My extremely wildarsed guess is that this is part of hacking investigation, possibly even the alleged Iranian hacking of power companies in the US (those stories were first reported in early May).
I say that because cybersecurity is a big part of what Verizon Enterprise (as I believe they now go by) sells to its business customers; the infographic above, warning of data breaches when you least expect it (heh), is part of one they use to fear-monger its customers. Energy consumers are one of its target customer bases. And the case studies it describes involve several Smart Grid projects. Precisely the kind of thing the government is most freaked out about right now.
After all, aside from Medicare fraud, the government simply doesn’t investigate businesses, ever. Certainly not the kind of bankster businesses we’d like them to investigate. One of the few things they investigate business activities for is to see if they’ve been compromised. Moreover, the Section 215 order requires either a counterintelligence or a counterterrorist nexus, and the government has gone to great lengths to protect large businesses, like HSBC or Chiquita, that have materially supported terrorists.
Anyway, that’s all a wildarsed guess, as I said.
Ah well. If the government can use Section 215 orders to investigate all the Muslims in Aurora, CO who were buying haircare products in 2009, I’m sure big business won’t mind if the government collects evidence of their crimes in search of Iran or someone similar.
Update: Note, this order seems to show a really interesting organizational detail. This is clearly an FBI order (I’m not sure who, besides the FBI, uses Section 215 anyway). But the FISA Court orders Verizon to turn the data over to the NSC. This seems to suggest that FBI has NSA store and, presumably, do the data analysis, for at least their big telecom collections in investigations. That also means the FBI, which can operate domestically, is getting this for DOD, which has limits on domestic law enforcement.
Comments:
What will Republicans do? And Democrats for that matter? This will be interesting, I really can’t imagine what’s going to happen
From the warrant:
“all call detail records or “telephony metadata” created by Verizon for communications (i) between the United States and abroad; or (ii) wholly within the United States, including local telephone calls”
The bothersome part is part (ii). Calls located wholly in the US, and including local telephone calls?
That sounds more like secondary and tertiary tiers of community of interest connections.
This is very special, by the Authorities. And I call it not just a Scoop, but a Meta-Scoop. Note that they do not require Verizon to give up calls from other countries that are not to or from the USA.
And it is absolutely VERBOTEN to reveal this secret order. Anyone who does reveal it will be subject to secret rendition. So oh…
Boy oh boy, reading that Greenwald piece I sure am glad that I only post stuff anonymously under a clever “handle”. Can’t be too careful these days. Oh, and that I haven’t done anything wrong, so I couldn’t have anything to worry about. Thank goodness the guys getting these subpoenas are from the government and are here to help me! See ya, 2-1/2 Men coming on soon!
@natasha1: we can’t assume that other orders were served because there isn’t proof. We can certainly estimate and conjecture, but we don’t just assume the worst of everything; that’s what the government does.
Emptywheel, would you mind contacting Glenn Greenwald about this truly obnoxious and false part of a Time article (http://newsfeed.time.com/2013/06/05/7-things-to-know-about-the-governments-secret-database-of-cellular-data/) on this subject?
I think Glenn should get them to publicly and profusely apologize:
“7. The Guardian‘s Glenn Greenwald had the scoop: Greenwald, an American columnist for the British newspaper, has a long history of challenging the surveillance state. Originally a supporter of George Bush and the Iraq War, he wrote a scathing indictment of government overreach in his 2006 book How Would a Patriot Act? During the Obama years he’s frequently criticized the President for infringing on civil liberties.”
Glenn, a supporter of Bush and the Iraq war? What utter nonsense!
It has nothing to do with Iran, China, terrorism, external threats … It has everything to do with developing a basis to prosecute any and everyone when we act up after the collapse of the dollar, when it really hits the fan ,..
Revealed: NSA collecting phone records of millions of Americans daily
In a letter to attorney general Eric Holder last year, they [Wyden and Udall] argued that “there is now a significant gap between what most Americans think the law allows and what the government secretly claims the law allows.”
“We believe,” they wrote, “that most Americans would be stunned to learn the details of how these secret court opinions have interpreted” the “business records” provision of the Patriot Act.
Coleen Rowley was speaking to Glen Ford, about drones and the ‘drone memo’, but her observation holds across all of Barack the Mob Lawyer Obama’s ‘memos’ …
Listen to Black Agenda Radio on the Progressive Radio Network, with Glen Ford and Nellie Bailey – Week of 6/3/13
You know, here’s what I’ve seen that’s been going on – and this began under Bush and I think Obama said “Well, that’s a good idea, I think I’m going to copy it. It’s ‘legalizing’ … So there were many actions that were completely, highly illegal – torture is one, torture is jus cogens, that means there is no excuse, that means there is no ticking time-bomb, no emergency – there is absolutely no possible way you can legalize torture, and yet John Yoo and his cohorts wrote memos and in, at the very least, years later when they became public it was then a fall-back – one of the lawyers called it : “It’s our golden shield.” And so all of the officials who followed thes unlawful memos were able then to say, “Well, sure. It was bad advice. But we were just following this bad advice. … And all of the Bush administration people have so far relied upon that theory of following bad advice : ‘our golden shield’.
And I think Obama came along and said hmm, that worked really well, I’m going to do the same thing … what they will all say is “I was relying on bad legal advice.”
Well, I worked in the FBI for 24 years, and there were such things as attorneys who were actually hired by the mob – they were kind of corporate attorneys for the mob – and there is no such defense as following attorneys’ advice when the attorneys were a part of it. …
Acting beacasue some stooge lawyer you’ve hired to explain to you that doing stuff that violates the Consitution’s Bill of Rights is ‘OK’ because of whatever ad hoc malarky … doesn’t cut it. Especially not for a Harvard Constitutional Law Lecturer … that’s a ticket to the Big House, not the White House.
The problem is that not only is the executive mobbed up, not only is the legislative mobbed up … the judicial is mobbed up as well.
” … whenever any Form of Government becomes destructive of these ends, it is the Right of the People to alter or to abolish it, and to institute new Government, laying its foundation on such principles and organizing its powers in such form, as to them shall seem most likely to effect their Safety and Happiness.”
There are 546 mobbed-up people in Washington who need to be replaced by ordinary Americans. The entire political class is corrupt. We’re the only ones here. We’re just going to have to do it ourselves. And then keep on doing it ourselves. That’s the way it’s spozed to be and the only way it has a chance of working.
Someone WaPo talked to describes it as20072006:
An expert in this aspect of the law said Wednesday night that the order appears to be a routine renewal of a similar order first issued by the same [FISA] court in 2006. The expert, who spoke on the condition of anonymity to discuss sensitive issues, said that the order is reissued routinely every 90 days and that it is not related to any particular investigation by the FBI or any other agency.
Report: Verizon providing all call records to U.S. under court order, Washington Post, June 2013
Though that would be except for pesky details about probable cause, and not Hoovering everything, and stuff:
Under the new plan, Gonzales said, the secret court that administers the Foreign Intelligence Surveillance Act, or FISA, will oversee eavesdropping on telephone calls and e-mails to and from the United States when “there is probable cause to believe” that one of the parties is a member of al-Qaeda or an associated terrorist group.
Court Will Oversee Wiretap Program, Washington Post, January 2007
At least, for the pesky details, so far as we were told.
I think it’s reasonable to assume that is is just one of a set of court orders that are issued on a regular basis. A separate order for each telecom company, or division of a telecom company. All of them regularly and routinely renewed.
It seems likely that such a very broad order is the way that TPTB cover themselves. And there’s that switch in San Francisco gathering up everything in bulk. I doubt there is a court order for that. We did hear that when the Bush admin came under so much pressure, they broke the surveillance program into pieces. Maybe they get the meta data from the telecoms who format it very nicely for them and make it easy to load into data bases, etc. and some agencies can use that info. The big data base (boy is that an understatement) might be reserved for the super cool intel analysts.
All a wild assed guess, since we’re doing wild assed guesses.
“Under the new plan, Gonzales said, the secret court that administers the Foreign Intelligence Surveillance Act, or FISA, will oversee eavesdropping on telephone calls and e-mails to and from the United States when “there is probable cause to believe” that one of the parties is a member of al-Qaeda or an associated terrorist group.”
To be fair, as long as a single call or email during the life of a court order involves a member of Al-Qaeda or its sales team affiliate downline, then this statement is true.
I see the docket number is 13-80, I wonder if the court started with 1. :o)
Another noteworthy part of this story is the fact that all 3 branches of government are onboard with this type of dragnet surveillance of American domestic communications.
The Executive branch, Congress, and the Courts all willfully and criminally in opposition against the Constitutional rights of the American public they’re supposed to be working for.
I wonder if we should now call all 3 branches of the US government unlawful enemy combatants? It sure seems like they’ve declared war on us.
@Snoopdido: Defending the indefensible – White House defends collecting phone records (http://hosted.ap.org/dynamic/stories/U/US_NSA_VERIZON_PHONE_RECORDS?SITE=AP&SECTION=HOME&TEMPLATE=DEFAULT&CTIME=2013-06-06-06-55-32):
“The White House on Thursday defended the National Security Agency’s need to collect telephone records of U.S. citizens, calling such information “a critical tool in protecting the nation from terrorist threats.”
While defending the practice, a senior Obama administration official did not confirm a newspaper report that the NSA has been collecting the telephone records of millions of U.S. customers of Verizon under a top secret court order.”
@Snoopdido: More “official US government” comments from CNN (http://www.cnn.com/2013/06/06/politics/nsa-verizon-records/?hpt=hp_t1):
“While the report infuriated people across the country — former Vice President Al Gore called the idea “obscenely outrageous” — a senior official in the Obama administration defended the idea of such an order early Thursday.
Without acknowledging whether the order exists, the administration official emphasized that such an order does not include collection of “the content of any communications or the name of any subscriber. It relates exclusively to metadata, such as a telephone number or the length of a call.”
“Information of the sort described in the Guardian article has been a critical tool in protecting the nation from terrorist threats to the United States, as it allows counterterrorism personnel to discover whether known or suspected terrorists have been in contact with other persons who may be engaged in terrorist activities, particularly people located inside the United States,” the unnamed official said in a written statement to media.”
You know, the only way stuff like this ever gets stopped is when a Democrat in office uses it against Republican targets, right?
So we can only hope that this data is being filtered for evidence of insider-trading.
Yeah, crazy-talk, I know.
Glad to see something’s finally got everyone’s attention. Now that a tree is visible, please step back and look at the forest.
NSA’s had it all for years, meta data and content, cell and land line. Could that be a big piece of what’s going into Beef Hollow Road? All your other electronic transactions make up some of the rest.
Cell’s been had since before 9/11. Starting with the FCC Act of 1934, if you don’t want someone to listen to something, don’t broadcast it to them. No one has ever had any expectation of privacy on a cell phone, or a wireless handset on a land line, or WIFI.
Room 641A opened for business in 2003. Whatever illusions of land line privacy, voice or data, anyone had disappeared then.
There are a lot of very bright folks at NSA. Since early in WWII they have earned their living by developing more capabilities than their targets believed possible. After 9/11 they were given a new mission and cubic money to achieve it.
Frank Church: “The NSA’s capability at any time could be turned around on the American people, and no American would have any privacy left, such is the capability to monitor everything…”.
Remember the “gloves come off” order? Think that might have been domestically too? After all, it was a Global War on Terror.
Even conservatives are arising (Other than Rand Paul and Darrell Issa aside as unserious contrarians)
Orrin Kerr;
“3) If the order is what it appears to be, then the order points to a problem in Section 1861 that has not been appreciated. Section 1861 says that the “things” that are collected must be relevant to a national security investigation or threat assessment, but it says nothing about the scope of the things obtained. When dealing with a physical object, we naturally treat relevance on an object-by-object basis. Sets of records are different. If Verizon has a database containing records of billions of phone calls made by millions of customers, is that database a single thing, millions of things, or billions of things? Is relevance measured by each record, each customer, or the relevance of the entire database as a whole? If the entire massive database has a single record that is relevant, does that make the entire database relevant, too? The statute doesn’t directly answer that, it seems to me. But certainly it’s surprising — and troubling — if the Section 1861 relevance standard is being interpreted at the database-by-database level.”
Not entirely surprising this came out now and that the government is being decidedly low-key in complaining about it. The government got a huge hole knocked in the Fourth Amendment the other day when the S.Ct. went 5-4 for taking and retaining DNA from everyone arrested, for later testing. Recall, the analysis in that case – and the main analytical support the majority relied upon – was that the police were going to use that DNA information to identify whether the arrestee was involved in another crime sometime in the past (from which DNA had been gathered*). In other words, just like the use of communications metadata to find who people using the phone have been talking to sometime in the past (for whatever crime-solving the government might want to dream up months or years after the fact), the DNA samples were to be used to identify who had left their DNA at a crime scene some time in the past.
If you read Scalia’s dissent this week in the DNA case (one of his blind-squirrel-finding-an-acorn moments), you’ll note he inveighs against creating a genetic panopticon at some length and with characteristic vigor. Not surprising people have referred to the communications collections which have been publicized, as a panopticon.
From the government’s perspective, all this disclosure does is (a) make clear to the public more of the contours of the police state which exists and serve as a warning to anyone who might hink about challenging it and (b) give them an excuse to start another leak investigation to charge a journalist criminally for having the temerity to consider exercising the First Amendment.
Glenn and the Guardian should lawyer up.
- – - -
* Note also – many people are unaware of this – that among the many politicians-showing-how-tough-on-crime-they-are bills which have been enacted into law are provisions removing the statute of limitations on criminal prosecution for crimes where some of the evidence is DNA evidence. Of course, since collection of DNA samples at crime scenes is now pretty much routine, that pretty much guts the idea of statutes of limitations.
@ scribe
“was that the police were going to use that DNA information to identify whether the arrestee was involved in another crime ”
Or if you talked to the arrestee in the past, and could possibly be extorted into providing your own surveillance.
“Become a confidential informant, or else”
If the order was specifically for the Boston Bombing then the order would included the Call Detail Records (the meta-data) for phone calls placed well in advance of the actual bombing.
That it doesn’t, supports a case that the data collection is an ongoing activity or isn’t related to the bombing at all.
Telecoms routinely keep these CDRs actively available for months (are longer) after calls are made – for their own billing, network support and customer support purposes.
The CDRs are then archived under Federal law depending on the type telecoms entity from anything from 3yrs to 7yrs although you would to consult with someone that is familiar telecoms law if this is important to you.
To my knowledge, the telecoms do not have the means to record broad swathes of the content of phone calls. Typically they might record individual calls or possible those associating with a customer call center. They really don’t want the liabilities that accrue from holding on to record calls.
The NSA, on the other hand, has the means to record large volumes of phones conversations has had been well documented for years. And has the means to transcribe the calls and search for specific information.
What the telecom provided CDRs do is to provide the NSA the ability to associate the call conversation with the meta-data of the CDRs. To provide as complete a picture of the call as possible.
It may be that the NSA has the necessary technical means to generate the CDRs themselves but even for telecoms this a massive operation which requires constant supervision so I suspect that NSA doesn’t have this means or at the least doesn’t have a robust means of their own.
@scribe: So, long ago you talked to someone who is now of interest and called in an order from a pizza joint Occupy folks frequented from a gym the 9/11 muscle worked out at.
Does that generate a knock on the door, a signature strike? A little dramatic perhaps, but illustrative.
All information, however obtained, is retained and becomes part of dynamic predictive analysis. Criteria are continually updated and ever more data integrated. As with DNA, no statute of limitations, fast data storage is amazingly elastic, and search algorithms ever more sophisticated.
Your nom de blog will not protect you. Ask the Google, then think about what someone with real national technical means knows.
The routine metadata from the communications companies serves as an index to the separately recorded signals from the public airwaves. Almost every phone call enters the public airwaves somewhere, whether wireless or microwaves or sat uplink. That’s all freely recorded, no warrant needed, no privacy. But it is a big jumble that needs sorting out – the metadata does this.
Most of this data collection has been going on since Oct. 4 2001, and some of it all the way back to WW2. Read James Bamford’s books on the NSA, it’s all explained there in detail.
@Netmaker: Nice logic.
One thought: “so I suspect that NSA doesn’t have this means or at the least doesn’t have a robust means of their own.” The grunt work meta data collection has already been done by the telecoms. Why expend the time and resources to reinvent that wheel? Maybe NSA is taking what is freely available from the telecoms and putting its talent and resources elsewhere. Stuff like using that data to decide who they want to pay more attention to, or deciding which phones to turn into personal bugs.
@tjallen You got it. Please add Kahn’s “The Codebreakers” to all of Bamford in the required reading list.
- @Jim White: Don’t give up hope, the perp hasn’t been caught. There’s still time for an interview. Perhaps this post will precipitate one now that you’ve pointed out some of the dots. Nah, they closed the case along with Ivins. Could be they knew where the orders came from, so didn’t need to talk to you, and didn’t dare chase back to the OEOB.
Curious isn’t it? Like not getting a facial recognition hit on the Tsarnev’s drivers license photos. May be a good way to distinguish which issues NSA is interested in and where FBI is driving. Turf is turf.
PS. Can you keep the little boogers from destroying my garden?
Feinstein told reporters at a Capitol Hill news conference today that the order was a three month renewal of an ongoing practice. Reuters.com reports the Intel committee members all thought it was a good thing.